사이버위협 정보공유 규격 STIX/TAXII의 업데이트 버전 발표
[보안뉴스 민세아] 美 국토안보부는(DHS) MITRE를 통해 사이버위협 정보공유 규격인 STIX/TAXII의 업데이트 버전을 발표했다.
MITRE는 지난 5월 사이버위협 정보표현 규격인 STIX를 기존 버전 1.0.1에서 현재 버전 1.1으로 1년여 만에 업데이트했으며, 7월에는 美 사이버위협 정보전송 규격인 TAXII 수정본을 발표했다.
이번 업데이트에서는 TAXII의 XML 메시지 정보 전송을 위한 바인딩 부분을 포함한 2가지 바인딩 스펙 오류를 수정하고, STIX의 8개 주요 구성요소들에 일괄적으로 이름(Title), 설명(Description), 요약설명(Short Description) 속성을 추가해 통일성을 부여하고 구성요소 파악의 이해도를 높였다.
▲STIX의 8개 주요 구성요소간의 관계도
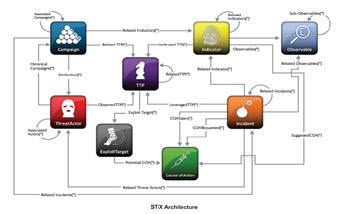
또한, STIX의 8개 주요 구성요소들 중 공격기법 관련 구조체인 TTP(Tactics, Techniques and Procedure)에 식별자 관련(id 및 idref) 정보의 부여가 필요한 항목이 있음을 인식하고 식별자를 부여했다.
이와 함께 STIX의 8개 주요 구성요소들 중 공격자 관련 구조체인 Threatr Actor에 공격자의 정교함을 표현하기 위해 sophistication 속성을 추가했으며, 원본문서를 그 역할 등에 따라 볼 수 있도록 정보출처 속성을 개선했다.
이와 관련해 보다 자세한 사항은 한국인터넷진흥원 인터넷침해대응센터 홈페이지나 아래 출처 내용을 참조하면 된다.
[출처]
1. https://taxii.mitre.org/specifications/version1.1/
2. http://stix.mitre.org/about/documents/STIX_Whitepaper_v1.1.pdf
3. http://stix.mitre.org/language/version1.1/
4. http://stix.mitre.org/language/version1.1/xsddocs/XMLSchema/ttp/1.1/ttp.html
5. http://stix.mitre.org/language/version1.1/STIX_1.1_Release_Notes.pdf
6.http://stix.mitre.org/language/version1.1/xsddocs/XMLSchema/threat_actor/1.1/threat_actor.html
[용어설명]
MITRE : 미 연방정부의 지원하에 R&D사업을 펼치는 비영리단체
STIX(The Structured Threat Information eXpression) : 사이버위협 정보표현 규격
TAXII(Trusted Automated eXchange of Indicator Information) : 사이버위협 정보전송 규격
관련 TTP 속성 : 공격패턴(Attack Patterns) 및 악성코드(Malware), 악성행위(Exploits), 공격기반 (Infrastructure) → 예를 들면, Attack Patterns은 식별자를 부여받은 단위 Attack Pattern의 조합들로 구성. 이를 통해 자칫 분석가별로 다양하게 기술될 수 있었던 공격기법에 대한 작성이 레고처럼 규격화된 단위정보들의 조합으로 구성이 가능하게 된다.
[민세아 기자(boan5@boannews.com)]
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>











 민세아기자 기사보기
민세아기자 기사보기



































 [2024-09-20]
[2024-09-20]