OpenSSH Client, 메모리 정보 노출 등 2개의 취약점 업데이트 발표
[보안뉴스 김경애] OpenSSH Client에서 메모리 정보 노출 취약점 등 2개의 취약점을 해결한 보안 업데이트를 발표했다.
해당 취약점은 roamin_common.c 안의 resend_bytes 함수에서 메모리 정보가 노출(Information leak)되는 취약점(CVE-2016-0777)과 roamin_common.c 안의 roamin_read 함수와 roaming_write 함수에서 힙 버퍼오버플로우(heap-based buffer overflow)가 발생하는 취약점(CVE-2016-0778)이다.
영향받는 버전은 OpneSSH 5.x, 6.x, 7.x ~ 7.1p1이다.
따라서 낮은 버전 사용자는 OpneSSH 7.1p2 로 업데이트하고, Roming 기능을 비활성화해야 한다.
이와 관련 좀더 자세한 사항은 한국인터넷진흥원 인터넷침해대응센터에 문의(국번 없이 118)하면 된다.
[용어 설명]
버퍼 오버플로우(Buffer Overflow): 특정 프로그램에 할당된 메모리 영역을 초과하는 크기의 데이터를 입력시킴으로써 발생하는 취약점
[참고사이트]
http://www.openssh.com/txt/release-7.1p2
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-0777
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-0778
[김경애 기자(boan3@boannews.com)]
[보안뉴스 김경애] OpenSSH Client에서 메모리 정보 노출 취약점 등 2개의 취약점을 해결한 보안 업데이트를 발표했다.

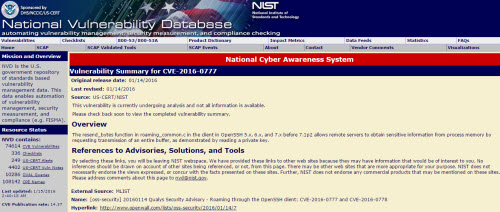
▲CVE-2016-0777 취약점 요약 화면(출처: NIST)
해당 취약점은 roamin_common.c 안의 resend_bytes 함수에서 메모리 정보가 노출(Information leak)되는 취약점(CVE-2016-0777)과 roamin_common.c 안의 roamin_read 함수와 roaming_write 함수에서 힙 버퍼오버플로우(heap-based buffer overflow)가 발생하는 취약점(CVE-2016-0778)이다.
영향받는 버전은 OpneSSH 5.x, 6.x, 7.x ~ 7.1p1이다.
따라서 낮은 버전 사용자는 OpneSSH 7.1p2 로 업데이트하고, Roming 기능을 비활성화해야 한다.
이와 관련 좀더 자세한 사항은 한국인터넷진흥원 인터넷침해대응센터에 문의(국번 없이 118)하면 된다.
[용어 설명]
버퍼 오버플로우(Buffer Overflow): 특정 프로그램에 할당된 메모리 영역을 초과하는 크기의 데이터를 입력시킴으로써 발생하는 취약점
[참고사이트]
http://www.openssh.com/txt/release-7.1p2
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-0777
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-0778
[김경애 기자(boan3@boannews.com)]
<저작권자: 보안뉴스(www.boannews.com) 무단전재-재배포금지>

.jpg)

.jpg)







 김경애기자 기사보기
김경애기자 기사보기



































 [2024-11-01]
[2024-11-01]