오늘의 키워드 : 이슬람, 미국, 프랑스, 오바마, 코렐, MS, 구글
오바마는 강력한 사고 보고 체계 원하고, 군 부대는 해킹 당하고
MS와 구글 사이에 이어지는 신경전, 그 사이로 코렐 취약점 발견
[보안뉴스 문가용] 지금 세계는 이슬람 극단주의 세력과의 전쟁 중입니다. 이슬람 극단주의 세력들은 아직도 프랑스의 웹 사이트를 공격하고 있고 미국의 중부사령부 트위터 계정까지도 훔쳐냈습니다. 소니 사건까지 얼마 전에 겪은 오바마 대통령의 발걸음이 더욱 바빠지고 있습니다. 특히 이제부터는 사고를 당한 사람은 철저하게 사고 내용을 보고하도록 법을 만들겠다고 나서고 있습니다. 십자군 시대도 아니고 일부 이슬람 극단주의자들과 서양 국가들의 이런 대치 상황을 보고 있자니 사람은 그냥 새로운 장만 만들어 놓으면(여기서는 인터넷) 했던 짓을 똑같이 반복하는 것밖에는 안 되는구나, 하는 생각이 듭니다.
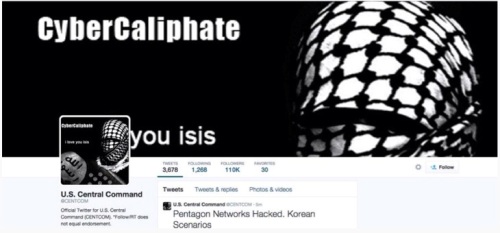
▲ 미 중부사령부 트위터 계정 첫 화면
한편 MS와 구글의 신경전이 계속되고 있습니다. 구글은 ‘우리가 90일 안에 공개한다면 하는 거니까 아쉬우면 너네가 90일 안에 패치를 배포해’라는 입장이고 MS는 ‘패치보다 취약점이 먼저 공개되면 누군가 패치가 나올 때까지 그 취약점을 통한 공격을 감행할 텐데 사용자 입장은 어쩌면 그렇게 생각을 못하는가’라며 비난하고 있습니다. 구글이 90일이라는 ‘내부 규정’을 외부에도 적용하는 게 오만해 보이기도 하지만 멀리 보면 취약점을 조금 더 빨리 없애는 데 도움이 될 것 같기도 해서 판단이 쉽지는 않습니다. MS 말대로 두 고래의 싸움에 사용자의 새우등만 터지지는 아닐까 걱정됩니다.
1. 미국 중부사령부의 계정 해킹당하다(CU Infosecurity)
http://www.cuinfosecurity.com/us-central-commands-accounts-hacked-a-7779
ISIS 지지 세력들, 미국 중부사령부의 트위터와 유튜브 계정 탈취(SC Magazine)
http://www.scmagazine.com/us-central-command-social-media-accounts-hacked/article/392128/
미국 중부사령부 트위터 피드 해킹한 사이버 지하드(CSOOnline)
http://www.csoonline.com/article/2867561/disaster-recovery/u-s-centcom-twitter-feed-compromised-by-cyber-jihadists.html
ISIS 지지 세력들, 미국 중부사령부의 트위터 및 유튜브 계정 탈취(Security Week)
http://www.securityweek.com/pro-isis-hackers-compromise-us-centcom-twitter-youtube-accounts
‘각오하라, 미군들’ 미국 중부사령부 트위터 계정 탈취당해(The Register)
http://www.theregister.co.uk/2015/01/12/us_centcom_twitter_account_hacked/
어제 미국의 군소 및 주류 언론사의 여러 계정들을 해킹하는 것으로 알려진 사이버칼리페이트(CyberCaliphate)라는 해커 단체에 대한 클리핑 기사가 나갔었죠. 그 단체가 FBI의 데이터베이스까지 손을 댔다고 호언장담하는 걸 두고 분석가들은 ‘키보드 워리어’짓이라고 판단했는데요, 그 키보드 워리어짓이 미국의 중부사령부의 트위터 계정까지도 싹 털었다고 합니다. 어제까지 낙관하는 자세로 사태를 관망하던 분석가들의 얼굴 표정이 궁금하기도 합니다. 미국 측은 그저 소셜미디어 계정 몇 개가 털린 것뿐이며 군사 비밀에 이르게 하는 네트워크까지는 아직 괜찮다고 발표했습니다. 현재 인터넷에 유포되고 있는 군사 기밀 정보들은 전부 가짜이며 해커들이 진짜처럼 보이기 위해 리패키징 한 것뿐이라고 합니다. 그러면서 또 이 모든 일들이 단순히 “협박 행위”일 것이라고 분석했는데, 이건 안이한 걸까요 아니면 긍정의 왕인 걸까요.
2. 오바마 대통령, 유출 사고 보고 및 패치 법으로 통일 요구(Infosecurity Magazine)
http://www.infosecurity-magazine.com/news/obama-to-unify-breach-reporting/
오바마 대통령 유출 통보 표준 제안(Threat Post)
http://threatpost.com/president-proposes-national-breach-notification-standard/110363
유출 사고가 있었다고? 그러면 얼른 말해야지 - 오바마(The Register)
http://www.theregister.co.uk/2015/01/12/obama_pushes_mandatory_breach_disclosure_laws/
오바마 대통령, 국가 유출 사고 통보 법과 학생 프라이버시 법 제안(SC Magazine)
http://www.scmagazine.com/state-of-the-union-speech-will-outline-privacy-and-data-protection/article/392127/
오바마 대통령 유출 통보 법제화 하기 원해(CU Infosecurity)
http://www.cuinfosecurity.com/obama-seeks-to-nationalize-breach-notification-a-7774
오바마 대통령, 국가 정보 유출 통보 법 제안해(Security Management)
https://sm.asisonline.org/Pages/Obama-Calls-for-Federal-Data-Breach-Notification-Law.aspx
어제 잠깐 클리핑 된 기사 내용입니다. 다만 어제는 비공식적인 루트를 통해 익명의 백악관 관계자가 제보해준 내용이었고, 오늘은 그게 오바마 대통령이 공식 석상에서 정식으로 발표했다는 차이가 있습니다. 결국 개인 유출 사고 시 통보 및 보호법을 통과시키겠다는 의지를 표명한 것입니다. 어제 자포스라는 의류 업체가 대규모 정보 유출 사고에 있어 어느 정도 책임을 져야 한다는 판결이 있었는데요, 오바마 대통령의 이 법안이 통과되고 나면 이제 정보를 관리하는 자의 책임뿐 아니라 싫든 좋든 자신이 도난당하지 않을 책임을 다 하지 못했다는 사실까지도 어쩔 수 없이 공유해야 합니다. 오바마 대통령은 학생들의 프라이버시 법까지도 함께 제안함으로써 프라이버시에 대한 균형도 잘 맞추었는데요, 참 능수능란합니다.
3. 사이버 지하드들, 수백 개의 프랑스 웹 사이트 공격(Security Week)
http://www.securityweek.com/cyberjhadists-hack-hundreds-french-websites
프랑스에서 이슬람 극단주의 세력과의 충돌이 계속해서 일어나고 있습니다. 샤를르 사태에 이어 프랑스의 웹 사이트 수백 개가 극단주의에 빠진 이슬람 해커들에게 침투 당해 지금 프랑스 웹사이트들에는 “신은 없고 오직 알라만이 있다”라거나 “프랑스에게 죽음을”이라는 문구가 여기저기서 등장한다고 합니다. 이런 공격이 하나의 단체에서 감행하는 것이 아니라 빠르게 뭉쳤다가 다시 흩어지는, 마치 게릴라 같은 해커 그룹이 하고 있기 때문에 수사 및 체포에 어려움이 많다는 것이 프랑스 사이버 경찰의 설명입니다. 또한 짧은 기간 안에 이 정도로 규모가 큰 해킹 캠페인도 처음이라고 합니다. 프랑스가 새로운 사이버전의 무대가 되고 있습니다.
4. MS, 윈도우 취약점 공개한 구글에 쓴 소리(Infosecurity Magazine)
http://www.infosecurity-magazine.com/news/microsoft-hits-back-in-row-over/
MS, 구글의 윈도우 취약점 공개에 견책(Threat Post)
http://threatpost.com/microsoft-censures-google-for-publishing-windows-vulnerability/110347
어떻게 그럴수가! MS, 구글보고 입이 싸다고 비난(The Register)
http://www.theregister.co.uk/2015/01/12/google_microsoft_coordinated_vulnerability_disclosure_policy_battle/
MS, 취약점 공개한 구글에 거친 항변(CSOOnline)
http://www.csoonline.com/article/2867534/vulnerabilities/microsoft-blasts-google-for-vulnerability-disclosure-policy.html
얼마전 구글이 윈도우 취약점을 발견 후 90일만에 대중에게 공개한 일이 있었습니다. 그리고 지난 11일 구글의 프로젝트 제로(Project Zero)에서 또 다시 한 달도 안 된 기간 내에 윈도우 8.1의 취약점을 공개했습니다. 역시나 발견 및 MS 측에 통보 후 90일만에 공개한 것이라고 합니다. MS는 해당 취약점에 대한 패치를 13일에 진행할 예정이었다고 합니다. MS는 블로그를 통해 “같이 일을 해보려고 하지만 구글에서는 자기들의 방침만 고집한다”라며 “특별히 발표 시기를 늦춰 사용자들을 조금이라도 더 보호해달라고 요청을 했는데, 그 며칠을 기다리지 못했다”며 비난했습니다. 취약점이 공개되는 날과 고쳐지는 날 사이에 발생하는 해킹 시도를 원천 차단하자는 취지를 구글 측에서 이해를 못한다는 것입니다. “구글이 맞다고 해서 모든 사용자에게 맞는 것은 아니며, 구글은 좀 더 사용자 입장에서 생각할 필요가 있다”고 일침을 꼽기도 했습니다.
5. 코렐 제품에서 제로데이 취약점 발견(Threat Post)
http://threatpost.com/0-days-exposed-in-several-corel-applications/110348
코렐 소프트웨어 제품들에 보안 오류들 발견돼(Security Week)
http://www.securityweek.com/core-security-discloses-security-vulnerabilities-corel-software-products
국내에는 코렐드로우로 유명한 코렐의 제품에서 DLL 탈취 취약점이 발견되었다고 합니다. 해커들은 DLL을 탈취해 원격에서 임의 코드를 실행할 수 있게 되는데요, 아직 코렐에서는 이에 대한 응답이 없다고 합니다. 당연히 패치도 아직까지 나오지 않은 상태고요. 지금 위험 상태에 있는 제품들은 코렐드로우 X7, 코렐 포토페인트 X7, 코렐 페인트샵프로 X7, 코렐 CAD 2014, 코렐 페인터 2015, 코렐 PDF 퓨전, 코렐 비디오스튜디오 프로 X7, 코렐 패스트플릭이라고 합니다.
[국제부 문가용 기자(globoan@boannews.com)]
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>


.jpg)








 문가용기자 기사보기
문가용기자 기사보기


































 [2024-11-22]
[2024-11-22] .jpg)
.jpg)




.jpg)


.jpg)
.jpg)