소니 픽처스 잦은 해킹에 노출되고 구글은 잦은 솔루션 내놓고
레긴은 당분간 조사 및 분석 이어질 듯
[보안뉴스 문가용] 소니 픽처스가 또 당했습니다. 플레이스테이션이 당한 지 얼마 지나지 않았고 소니 픽처스 역시 불과 지난 해에 해킹에 대한 안 좋은 기억을 가져왔음에도 말입니다. 지금 해커로 보이는 일당과 협상 중에 있다고 하니 일이 어떻게 진행될지 궁금합니다. 물론 소니 자체에서도 그 협상 내용을 밝히지 않고 있어, 진실이 얼마나 알려질지 조금 회의적이긴 합니다만.
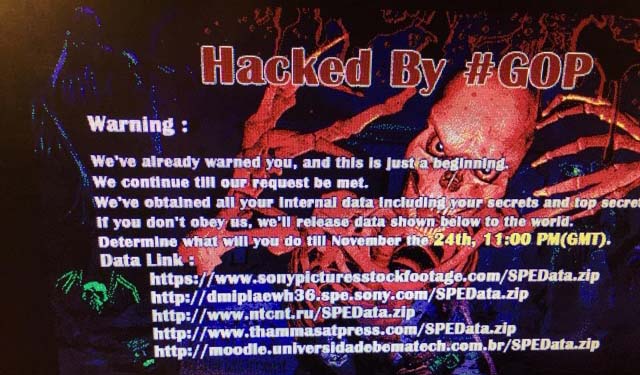
▲ 소니 픽처스 직원들이 출근해서 컴퓨터를 키자 나타난 화면
어도비는 긴급 패치를 배포했는데, 이는 지난 10월에 있었던 공식 패치에 대한 패치로 볼 수 있어 어떻게 보면 한 번에 일을 제대로 처리하지 못한 것으로도 보이고 패치의 패치라는 신개념 책임감을 보는 것도 같아 묘합니다. 또한 구글 역시 요즘 보안에 엄청난 투자를 하고 있는 듯한 모습인데요, 보안이 과연 내년에 얼마나 큰 이슈가 될 지 기대가 됩니다.
1. 소니 픽처스 해킹으로 네트워크 다운(Infosecurity Magazine)
http://www.infosecurity-magazine.com/news/sony-pictures-hack-shuts-down/
소니 픽처스 현재 네트워크 해킹 사태 점검 중(Threat Post)
http://threatpost.com/sony-pictures-dealing-with-apparent-network-compromise/109625
소니 픽처스, 해커 소행으로 네트워크 다운시켜(The Register)
http://www.theregister.co.uk/2014/11/25/sony_pictures_in_it_lockdown_after_alleged_hacker_hosing/
소니 픽처스, 기업 네트워크 해킹으로 차단(Security Week)
http://www.securityweek.com/sony-pictures-hack-leads-corporate-network-shutdown
소니 픽처스가 또 해킹당했습니다. 그래서 기업 전체의 네트워크 망을 차단하고 점검 중에 있습니다. 이번에 소니 픽처스를 해킹한 단체는 GOP(Guardians of Peace, 평화 수호자)라고 알려져 있습니다. 해킹당한 직원들의 컴퓨터에 “hacked by GOP”라는 메시지가 송출되었다고 합니다. GOP는 소니 픽처스의 비밀 정보를 훔쳐냈다며 자신들의 요구를 들어줄 것을 협박조로 요청하고 있습니다. 하지만 아직 요구 사항이 무엇인지는 아직 그 누구도 밝히고 있지 않습니다. 소니 픽처스는 2011년에도 룰즈섹(LulzSec)이란 그룹에 의해 해킹당한 적이 있고, 올해에는 소니 플레이스테이션 네트워크에 대한 공격으로 1억 건의 사용자 정보가 유출된 적이 있죠. 소니가 보안 강화에 어려움이 있는 건지, 아니면 소니의 콘텐츠가 그렇게나 매력적인 건지, 하여튼 해킹에 계속해서 시달리고 있습니다.
http://threatpost.com/adobe-releases-emergency-flash-player-patch/109623
어도비, 플리새의 하이잭 버그 죽이기 위한 긴급 패치(The Register)
http://www.theregister.co.uk/2014/11/25/thought_you_were_done_with_patching_this_month_adobe_can_fix_that/
어도비, 플래시 플레이어 패치로 방어막 강화(Security Week)
http://www.securityweek.com/adobe-patches-flash-player-add-additional-protection-against-attack
이번에는 윈도우, 맥, 리눅스 사용자 모두를 위한 패치이며, 해커가 원격에서 코드를 실행할 수 있도록 해주는 취약점이 수정되었습니다. 지난 달 14일에 어도비가 공식 패치를 내놓은 지 불과 1주일 만에 뚫려버리는 사태가 있었는데요, 한 달 만에 ‘긴급’ 패치가 또 이루어진 걸로 보아 지난 공식 패치로 다 다룰 수 없었던 문제가 또 있었음이 드러났습니다. 어도비 측에서도 “지난 10월에 있었던 패치를 좀 더 보완하는 성격의 패치”라고 합니다. 즉 같은 오류를 두 번에 걸쳐 해결했다는 것이죠. 이렇게 끈질기게 문제를 해결하는 건 앞으로 ‘업데이트’가 필수가 될 제작 산업의 표준이 되어야 할 것 같습니다.
3. 레긴 멀웨어가 주는 8가지 의문(CU Infosecurity)
http://www.cuinfosecurity.com/regin-espionage-malware-8-key-issues-a-7609
정부기관의 레긴 사용, 합법적인가?(Threat Post)
http://threatpost.com/experts-question-legality-of-use-of-regin-malware-by-intel-agencies/109566
아직도 레긴의 탄생지가 어디인지 밝혀지지 않은 가운데 여러 가지 논란만 확산되고 있습니다. 어제 밝혀진 “국가가 뒤를 봐주고 있다”, “모바일 네트워크를 노리고 있다”, “감지가 매우 어렵다” 등의 추정 및 사실 외에 벨기에 통신업체인 벨가콤(Belgacom)과 유럽의회가 공격당한 듯이 보인다는 것과 사실상 일반 사용자들에게는 큰 위협이 되지 않는다는 주장이 추가로 제기되었습니다. 또한 정부기관에서 이를 활용하는 것에 법적 근거가 있는가에 대해서도 논의 중에 있다고 합니다. 물론 대부분 부정적인 편에 서있긴 한 것 같습니다. 그래도 비난 일색이 아니라 ‘논의’ 상태가 이루어진다는 것이 놀랍긴 합니다. 레긴 관련 뉴스는 계속해서 나올 것 같습니다.
4. 구글, 앱스 사용자 위한 새로운 보안 툴 공개(Security Week)
http://www.securityweek.com/google-releases-new-security-tools-apps-users
구글리락스, 구글이 개발한 새로운 앱 보안 툴(The Register)
http://www.theregister.co.uk/2014/11/25/google_employs_security_wizard_for_apps_drops_intel_panels/
구글 앱스(Google Apps) 사용자들의 계정을 보호하기 위해 구글에서 새로운 보안 툴 두 개를 세상에 내놓았습니다. 하나는 어제자 글로벌 뉴스 클리핑에 언급된 ‘산타’이고 또 다른 하나는 디바이시즈 앤 액티비티(Devices and Activity)라는 대시보드입니다. 액티비티 대시보드는 최근 28일 동안 어느 기기, 어느 위치에서 계정 접속이 일어났는지 보여주는 기능을 가지고 있고, 현재 접속 기기에 대한 상세 정보도 출력합니다. 또한 보안 관련 사용자 설정을 매우 쉽게 해놓았다고 하는데, 이는 곧 사용자 리뷰 등을 통해 더 확실히 밝혀지겠죠. 구글이 정말 끊임없이 보안 관련 툴 및 솔루션을 내놓는데, 구글 정도의 회사에서 이렇게 보안에 집중을 할 정도면 뭔가 변화가 있지 않을까 기대가 되기도 하고, 구글의 영향력이 과연 어느 정도인지 가늠해보고 싶기도 합니다.
5. 크레이그즈리스트, DNS 하이재킹 당해(Infosecurity Magazine)
http://www.infosecurity-magazine.com/news/craigslist-dns-hijacker-leads/
크레이그즈리스트 하이재킹 당했으나 다시 서비스 시작(Threat Post)
http://threatpost.com/craigslist-back-online-following-dns-hijack/109559
크레이그즈리스트 사용자들, 악성 사이트로 우회돼(The Register)
http://www.theregister.co.uk/2014/11/25/craigslist_pushes_punters_to_youtube_hacker_site/
크레이그즈리스트는 개인 광고, 구인, 토론 등이 벌어지는 대형 커뮤니티 사이트입니다. 지난 주말, 우리나라 시각으로 월요일쯤에 해킹이 이루어진 것으로 보이는데요, 결과적으로는 사용자들을 전혀 다른 사이트로 우회시키는 데 성공했습니다. 그중 하나가 해커들의 커뮤니티인 디지털갱스터(DigitalGanster.com)인데, 뜻하지 않은 트래픽 증가 때문에 서비스가 중단되기도 했습니다. 디지털갱스터는 트위터 계정, 브리트니 스피어즈 공식 사이트 등을 해킹한 것으로 유명한 곳입니다. 이곳 운영자는 이번 사건과 관련이 없다고 주장하고 있는 상태입니다. 한국에도 사용자가 있을 것 같아서 덧붙이면, 계속해서 크레이그즈리스트에 접속이 불가한 경우 DNS 서버에 있는 craigslist.org와 craigslist.com 엔트리를 지우면 된다고 합니다.
[국제부 문가용 기자(globoan@boannews.com)]
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>











 문가용기자 기사보기
문가용기자 기사보기

































 [2025-04-07]
[2025-04-07]