오늘의 키워드 : 애플과 중국, 플래시, 안드로이드, PHP
사이버 범죄 대응하는 정부 단위 움직임 점점 커지고 있어
[보안뉴스 문가용] 애플이 그동안 조용하다 했더니 팀 쿡이 어제 중국 부총리를 만났군요. 그러면서 중국은 또 호주 변호사라는 시장을 개척했고요. 영국 국가기관은 경찰 경력 없어도 컴퓨터 기술 출중한 인재를 뽑고 있고, 이란에서는 국가 주요 시설 근처에서 스파이를 잡았다고 합니다. 안드로이드는 바람 잘날 없으니 아는 사람한테 오는 문자도 조심해서 받으세요. 어제는 경제, 오늘은 국가, 정보보안의 활동분야 스케일이 남다릅니다. 그만큼 해커들의 움직임은 더 빨라지고 있지요. 어도비 지난 주에 패치했는데 벌써 뚫리다뇨.
.jpg)
▲ “애플 사장 왔다며?” “쉿. 그냥 평상시처럼 행동해.”
1. 애플, 중국의 중간자 공격 인정(Infosecurity Magazine)
http://www.infosecurity-magazine.com/news/apple-admits-mitm-icloud-attack/
중국 당국이 애플의 아이클라우드를 통해 중간자 공격을 실행하고 있다는 걸 여러 전문가가 주장한 바 있지만 애플은 그 동안 계속 침묵을 지켜왔었죠. 적어도 중국을 언급하지는 않았습니다. 그러다가 드디어 공식적으로 인정했습니다. 하지만 아이클라우드 서버 자체가 그들 손에 넘어간 건 아니라고 합니다.
2. 팀 쿡, 베이징 방문해 중국 정부 인사 만나(Security Week)
http://www.securityweek.com/apple-ceo-meets-chinese-official-amid-icloud-hacking-row
애플과 중국의 신경전이 예사롭지 않은 가운데 팀 쿡이 중국 부총리를 만났다는 소식입니다. 바로 어제 일입니다. 대화 주제는 사용자의 정보 보호, 정보 및 통신 분야의 협동 강화였다고 중국 언론은 전하고 있는데요, 아직 애플의 공식 입장은 나오고 있지 않은 상태입니다. 이것 때문에 그동안 중국을 언급하지 않고 혼자 끙끙 앓아왔던 것도 같습니다.
3. 영국 국가범죄수사국(일명 NCA), 사이버 범죄 전담반 인원 늘려(Infosecurity Magazine)
http://www.infosecurity-magazine.com/news/nca-touts-for-new-recruits-to/
수사관 경력이 없더라도 인원을 확충하겠다는 NCA는 대신 소프트웨어 개발, 네트워크 엔지니어링, 디지털 포렌식, 온라인 수사 기술력을 갖춘 사람을 뽑겠다고 합니다. 사이버 범죄가 더 이상 기존 범죄의 곁가지가 아니라 주류 중 하나로 인지되고 있습니다. 좋아해야 하나 말아야 하나...
4. 이란 당국 원자로 보유 지역에서 사이버 스파이 체포(Security Week)
http://www.securityweek.com/iran-arrests-spies-province-nuclear-reactor
이란의 부시르 지역은 이란에서 유일하게 원자로가 존재하는 곳입니다. 그래서인지 이란의 경제, 산업, 군사, 상업의 허브라고도 불리지요. 바로 이곳에서 사이버 스파이들을 검거하는 데에 성공했다는데 아직 해커들의 국적과 숫자는 밝히지 않고 있습니다.
5. 지난 주 패치 된 플래시, 벌써 공략 시작(Threat Post)
http://threatpost.com/exploit-for-patched-flash-vulnerability-already-in-two-exploit-kits/108972
패치된지 이제 1주일밖에 안 지났는데, 벌써 플래시 취약점의 익스플로잇 킷이 돌아다니고 있습니다. 한 전문가는 패치가 이렇게 빨리 무용지물이 되어버리는 건 처음 보는 일이라고 합니다. 이미 해커들 사이에서는 이 취약점을 공략한 피에스타(Fiesta)와 앵글러(Angler)라는 익스플로잇 킷이 은밀하게 돌아다니고 있답니다.
6. NIST, 하이퍼바이저 보안 가이드 발간(Threat Post)
http://threatpost.com/nist-publishes-draft-hypervisor-security-guide/108966
하이퍼바이저란 프로세서나 메모리와 같은 다양한 컴퓨터 자원에 서로 다른 각종 운영 체계(OS)의 접근 방법을 통제하는 얇은 계층의 소프트웨어, 즉 다수의 OS를 하나의 컴퓨터 시스템에서 가동할 수 있게 하는 소프트웨어라고 네이버 백과에 나와 있네요. NIST에서 3년째 시리즈로 발간하고 있는 가상화 보안 가이드의 일환입니다. 이번 주에 나온 건 초안이고 대중의 의견을 수렴하는 건 11월 10일까지입니다.
http://threatpost.com/php-patches-vulnerabilities-including-remote-code-execution-flaw/108960
5.6.1, 5.5.17, 5.4,33버전에서 발견된 버퍼 오퍼블로우와 원격 코드 실행을 가능하게 하는 PHP의 취약점이 패치되었습니다. CVE-2014-3669, CVE-2014-3668, CVE-2014-3670이 주로 다뤄진 취약점이라고 합니다.
8. 안드로이드 이미지에 코드 숨김 가능(The Register)
http://www.theregister.co.uk/2014/10/22/android_can_be_tricked_into_loading_malware_obfuscated_in_pngs/
안드로이드 체제에서 악성 소프트웨어를 마치 이미지 파일인 것처럼 패키징 하고 은닉하는 걸 가능케 해주는 취약점이 발견되었습니다. 얼마 전 동영상 안에 데이터를 숨겨서 빼돌리는 기사가 보안뉴스에서 나갔는데요, 그것과 뭔가 비슷해 보입니다.
9. 중국 APT 단체, 호주 변호사들 공격(The Register)
http://www.theregister.co.uk/2014/10/21/bakers_dozen_of_apt_groups_popping_aussie_biz/
벌만 쫓아가면 꿀을 딸 수 있죠. 해커들 쫓아가도 마찬가지입니다. 중국이 호주 변호사들을 공격하고 있다면, 그곳에도 뭔가 꿀이 있다는 소리입니다. 아니나 다를까 여러 기업의 중요한 정보들이 다량으로 도난당했다네요. 앞으로 변호사 사무실도 안전하지 못하게 되었습니다.
10. 안드로이드 랜섬웨어 콜러(Koler)의 웜 버전 , SMS 통해 번져(SC Magazine)
http://www.scmagazine.com/worm-variant-of-android-ransomware-koler-spreads-via-sms/article/378785/
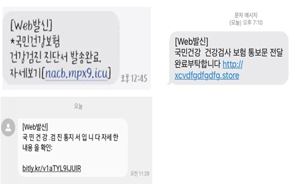
성인 사이트에 접속한 적이 있는 사용자를 주로 노린 화면 잠금형 랜섬웨어인 콜러가 발견된 건 지난 5월이었죠. 그런데 이 랜섬웨어가 웜의 형태로 지금 돌아다니고 있다는 소식입니다. 전화기에 콜러가 침입하면 그 전화기에 저장된 모든 연락처에 악성 문자를 보내고, 그 문자에 연결된 링크를 클릭하면 화면이 잠깁니다. 이제 아는 사람한테 문자가 와도 조심해야 합니다.
[국제부 문가용 기자(globoan@boannews.com)]
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>

.jpg)

.jpg)







 문가용기자 기사보기
문가용기자 기사보기



































 [2024-11-01]
[2024-11-01]