Risk IT 프레임워크는 1년 전에 ISACA 국제협회에서 IT 리스크 관리와 정보보호 리스크 관리를 위해 만들어낸 모델이다. 오늘날 거버넌스 시대의 확장과 불확실성이 지배하는 기업 환경에서 IT 리스크와 정보보호 리스크는 비즈니스 리스크로 바로 직결되는 사안으로 중요성이 더욱 높아지고 있다. 이에 본지에서는 IT거버넌스/컨설팅/감리법인 씨에이에스 컨설팅에서 근무하면서 관련 분야에서 왕성한 활동을 펼치고 있는 조희준 이사의 연재기고를 싣도록 한다. [편집자 주]
연재순서-----------------------
1. Risk IT 프레임워크
2. 정보보호에서의 Risk
3. Risk IT 프레임워크의 도메인 1
4. Risk IT 프레임워크의 도메인 2
5. Risk IT 프레임워크의 도메인 3
6. Risk IT 프레임워크와 정보보호의 연계
-----------------------------------
[보안뉴스=조희준 씨에이에스 이사] 요즘 들어 Risk라는 단어가 화두이다. 리스크? 왜 위험이라고 하지 않고 리스크라고 표현할까? 리스크의 의미는 불확실성(uncertainty)이다. 비즈니스의 목적 달성에 영향을 끼칠 수 있는 긍정적인 면도 부정적인 측면도 모두 가지고 있기에 리스크를 불확실한 것이라고 얘기하는 것이다. 위험(危險)이라는 국어로 표현하다 보면 리스크의 부정적인 면만을 나타내기 쉽다. 그래서 요즈음 리스크와 관련된 학회나 업계에서는 Risk를 그냥 ‘리스크’라고 표현하는 추세이다.
리스크 IT 프레임워크의 탄생
COBIT과 IT 거버넌스로 널리 알려진 ISACA(Information System Audit & Control Association : 정보시스템감사통제 국제협회 www.isaca.org)에서 IT 거버넌스의 프레임워크인 COBIT과 이를 확장한 Val IT, 그리고 다음으로 출시한 프레임워크가 바로 리스크 IT이다.
COBIT은 IT 거버넌스의 5대 목표인,
①전략적 연계
②가치 제공
③리스크 관리
④자원 관리
⑤성과 측정을 실무차원에서 설명하고 구현해내는 프레임워크이다.
COBIT의 목표

이를 구현하기 위해
①사업 요구사항
②IT 자원
③IT 프로세스의 3가지 차원으로 설명하고 있다.
COBIT 프레임워크
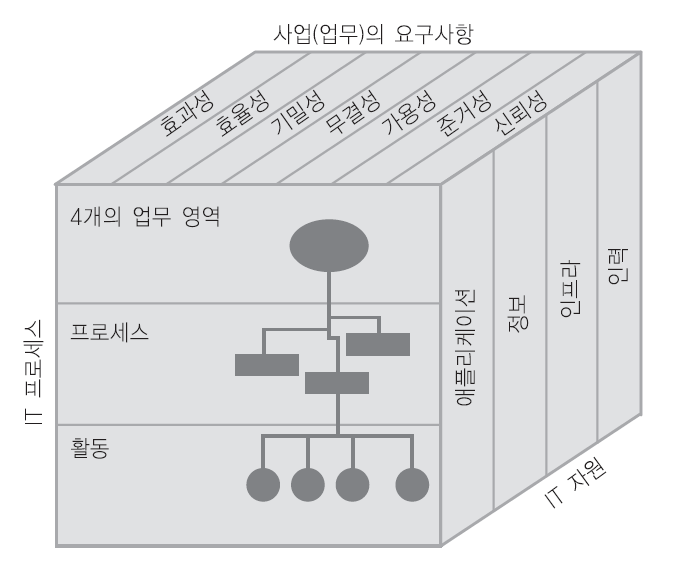
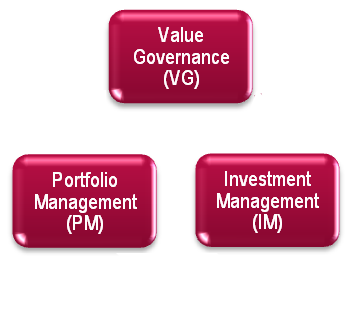
그 이후 IT 투자와 그에 따른 의사결정이 중요시됨에 따라 ‘② 가치 제공’을 경영자와 투자자 등의 이해관계자들을 위해서 만들어낸 2번째 프레임워크가 Val IT 이다. Val IT는 3가지 도메인으로 구성되어 있다.
①가치 거버넌스(Value Governance)
②포트폴리오 관리(Portfolio Management)
③투자 관리(Investment Management)
Val IT 프레임워크
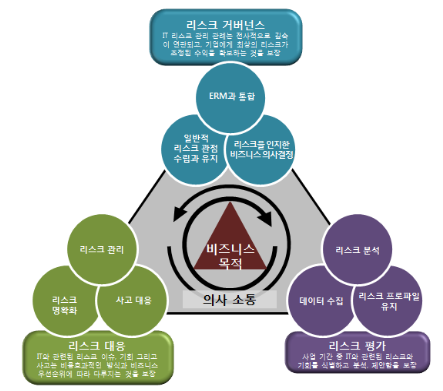
COBIT과 Val IT 이후에 ‘③ 리스크 관리’를 중점적으로 소화해 내기 위해 리스크 IT 프레임워크가 탄생했다. 조직의 외부적인 환경의 불확실성은 점점 커져만 가고 정보와 정보보호에 대한 리스크가 조직의 생존여부를 좌지우지하는 비즈니스 환경에서 리스크는 심도 있게 전문적으로 다루어져야 하므로 이에 대한 구체적인 프레임워크가 탄생된 것이다. 리스크 IT 프레임워크는 3가지 도메인으로 구성되어 있다.
①리스크 거버넌스(Risk Governance)
②리스크 평가(Risk Evaluation)
③리스크 대응(Risk Response)
리스크 IT 프레임워크
이번 연재기고를 통해 최근에 주목 받고 있는 리스크와 이를 통해 IT와 정보보호의 리스크를 심층 분석한 ‘리스크 IT 프레임워크’를 두루 살펴보기로 한다. 이를 통해서 정보보호를 도구나 기술로만 보는 차원에서 기업이나 공공기관의 중요한 전략으로 끌어올리는 기회가 되기를 바란다. 보다 자세한 내용은 http://www.isaca.org/와 www.isaca.or.kr 에서 찾아볼 수 있다.
[참고자료 및 출처]
www.isaca.org
www.isaca.or.kr
www.isc2.org
www.cisspkorea.or.kr
Information Security Governance, ITGI, 2008
CISM Review Manual, ISACA, 2009
The IT Governance Implementation Guide-Using COBIT® and Val IT 2nd Edition, ISACA, 2007
Official (ISC)2 Guide to the CISSP CBK, Auerbach Publications, 2007~2008
CISM 한글 Review Manual, ISACA, 2011
ISACA 지식용어집, ISACA 지식 FAQ, 한국정보시스템감사통제협회, 2009
IT 거버넌스 프레임워크 코빗 COBIT4.1을 중심으로, 인포더북스, 2010
정보보호 전문가의 CISSP 노트, 인포더북스, 2011
리스크 IT 프레임워크, 한국정보시스템감사통제협회, 2012
필자는 ---------------------------------------------------------------------------
 조 희 준 josephc@chol.com
조 희 준 josephc@chol.com
CIA, CRMA, CGEIT, CISA, COBIT, CISM, CRISC, CCFP, CISSP, CSSLP, ISO 27001(P.A), ITIL intermediate, IT-PMP, PMP, ISO 20000(P.A)
G-ISMS 심사원, BS10012(P.A), BS25999(P.A), CPPG
PMS(P.A), (ISC)2 CISSP 공인강사, 정보시스템감리원,
행정안전부 개인정보보호 전문강사
행정안전부/한국정보화진흥원 사이버범죄예방교화 전문강사
IT거버넌스/컨설팅/감리법인 ㈜씨에이에스 컨설팅 이사, 강원대학교 겸임교수, 세종사이버대학교 외래교수, 한양대학교 대학원 외래강사, (ISC)2 CISSP Korea 한국지부, (사)한국정보시스템감사통제협회, 한국포렌식조사전문가협회에서 활동하고 있다. IT감사, 내부감사, IT거버넌스와 정보보호 거버넌스가 주 관심분야이다, 이와 관련해서 컨설팅, 기고, 강의, 강연활동을 활발하게 펼치고 있다. 2010년 두 번째 단행본인 ‘IT거버넌스 프레임워크 코빗, COBIT’ 출간 후, 2011년에 ‘정보보호 전문가의 CISSP 노트’를 발간했고, 2012년 ‘리스크 IT 프레임워크’를 번역 출간했으며, 현재 고려대학교 일반대학원 박사과정에서 공부 중이다.
-------------------------------------------------------------------------------------
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>

.jpg)

.jpg)






 권준기자 기사보기
권준기자 기사보기


































 [2024-11-25]
[2024-11-25] 


.jpg)
.jpg)
.jpg)




.jpg)


