[보안뉴스 권 준] 전 세계 국가들의 보안위협 정도를 지수화한 세계 보안지도(Global Security Map)에서 우리나라는 어떤 위치를 차지하고 있을까?
HostExploit 그룹이 발표한 세계 보안지도 [출처 : HostExploit, "The Global Security Map - A Question and Answer Session on Cybercrime", 2012/6/23]
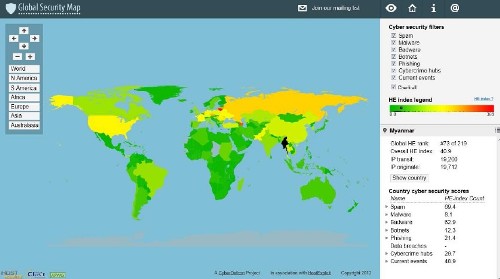
사이버 범죄 서버의 위치와 기능을 추적하는 연구기관인 HostExploit 그룹은 지역별로 사이버보안 위협 분포 및 수준을 시각화한 세계 보안지도를 지난 6월말 발표했는데, 여기서 우리나라는 26위인 것으로 나타났다.
한국인터넷진흥원(KISA)이 발표한 7월 1주차 인터넷 동향에 따르면 지난 6월 23일 공표된 세계 보안지도는 악성코드 호스팅 및 유포, 스팸, 봇넷, 피싱, 기타 공격활동 등을 HE지수로 평가하고, 보안위협 발생 근원지 정보를 기반으로 시각화한 것이다.
여기서 말하는 HE지수(HostExploit 지수)는 유해한 활동 발생 국가의 인프라 규모 대비, 발생하는 사이버 보안위협 수준을 0~1,000 사이 범위로 점수화한 지수로 0에 가까울수록 위협 정도가 낮은 지역임을 의미한다.
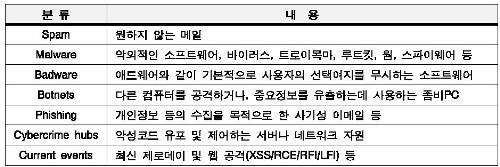
세계 보안지도의 평가기준이 되는 HE지수는 사이버 보안위협의 종류에 따라 구분되는데, 분류기준은 다음과 같다.
|
|
|
사이버 보안위협의 종류 [출처 : HostExploit, "The Global Security Map - A Question and Answer Session on Cybercrime", 2012/6/23, KISA Internet Weekly 7월 1주(20120705)] |
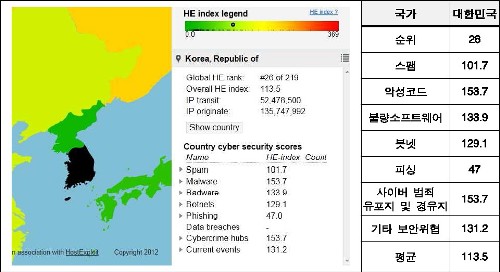
조사결과 사이버 보안위협의 발생우려가 가장 큰 나라는 리투아니아, 가장 적은 나라는 핀란드로 평가됐으며, 총 219개 나라 중 한국은 26위로, 미국(11위)과 중국(20위)에 비해 낮은 수준이나, 일본(64위)보다는 높은 위협수준을 나타내고 있는 것으로 조사됐다.
|
|
|
우리나라의 HE지수[출처 : HostExploit, "The Global Security Map - A Question and Answer Session on Cybercrime", 2012/6/23, KISA Internet Weekly 7월 1주(20120705)] |
전 세계적으로 러시아 및 동유럽 지역 국가에서 스팸 발송, 악성코드 유포지, C&C 등의 보안위협의 주요 근원지로 나타나고 있는데, 주로 사이버 침해에 관한 법률 및 처벌이 미비한 국가에서 보안위협 발생의 근원지가 되고 있는 것으로 나타났다.
[권 준 기자(editor@boannews.com)]
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>

.jpg)

.jpg)






 권준기자 기사보기
권준기자 기사보기


































 [2024-11-22]
[2024-11-22] 


.jpg)
.jpg)
.jpg)




.jpg)


